Categories
- Android (21)
- Animal (1)
- Application Android (7)
- Biology (4)
- Blogger (3)
- Computer (1)
- Conspiracy (1)
- Crop Circle (1)
- Download (1)
- Email (1)
- Food (3)
- Football (1)
- gadgets (2)
- Health Tips (3)
- Hollywood (1)
- Hosting (1)
- Internet (30)
- Internet Marketing (4)
- Islam Religion (1)
- Linux (9)
- Lyrics (6)
- Macintosh (1)
- mobile (3)
- Network Security (2)
- News (32)
- News. Celebs (2)
- PSSI (1)
- Ramadhan (7)
- Sains (2)
- Security (1)
- SEO (1)
- Showbiz (4)
- Smadav (1)
- Smartphone (1)
- Technology (6)
- Tips and Trik (26)
- Tips n Triks (3)
- Tourism (4)
- Ubuntu (8)
- World (1)
Blog Archive
-
▼
2011
(113)
-
▼
August
(73)
-
▼
Aug 15
(24)
- Clearing temporary Internet files and cookies
- Clearing visited Web sites history
- Locking down Internet Explorer
- Using WPA for a more secure wireless connection
- Using WEP for secure communication
- Disabling Messenger Service
- Disabling Remote Desktop connection
- Configuring Windows firewall
- Disabling Unneeded Protocols
- Assigning Alternative IP Addresses
- short names long meaning
- Maximize Dial-up Modem Settings
- Advanced Google Search
- Best 3 Ways online money
- Removing Stored User Name and Password in Mozila F...
- Auto Disconnect Internet Explorer
- Stop Windows Messenger Autostart
- Speed Up Internet
- Speed Up Internet
- Adjusting your cookie security policy
- Update My Computer
- Improving Web Site Security
- Promote Your Site For Free
- How to Secure Facebook Account
-
▼
Aug 15
(24)
-
▼
August
(73)
Feedjit
Total Pageviews
Clearing temporary Internet files and cookies
Every time you visit a Web site, the files for the Web page, such as the HTML and the images, are downloaded and stored in a temporary directory known as Temporary Internet Files. Over time, this directory can become full of images and HTML from various Web sites that you have visited. This directory can end up taking up a lot of space on your hard drive. Additionally, a user can browse your Temporary Internet Files directory and find out exactly what site you have been visiting just as if they were looking at your browser history. If you are concerned about your privacy, or just concerned about disk space, then clearing the Temporary Internet Files is a must.
Cookies are another item that is created on your computer when you visit a Web site. Contrary to popular belief, cookies are really not that bad. Most Web sites use them to save user data to a browser. One example of this is site preferences or automatic logon when you visit a Web site. The Webmaster of the Web site can detect if their Web site has already given you a cookie that has your user ID stored in it. If it finds one, then it knows exactly who you are and logs you on automatically. Advertisers also use cookies to store personal data. Instead of showing you the same advertisement 50 times, they use cookies to keep track of how many times an advertisement is displayed on your screen.
A common myth about cookies is that they allow Web sites to track other sites you visit. That is just not true. The only cost of having cookies on your computer is a privacy concern for local users. Any user that has physical access to your computer can browse to the directory that the cookies are stored and view what Web sites you visit because the cookies are named after the Web site that instructed your browser to put them on your computer.
Clearing the Temporary Internet Files and removing the cookies is a very simple task. Just follow these steps to clear these files:
1. Open up another copy of Internet Explorer.
2. Click Tools and then select Internet Options.
3. Under the Temporary Internet Files section, click the Delete Files button.
4. You will be prompted to confirm if you would also like offline files to be deleted. For maximum privacy, check the box and Click OK.
5. Once the files are erased, you will be shown the Internet Options screen again. Taking care of the cookies for your privacy is just as easy. Just click the Delete Cookies button.
6. Click OK on the confirmation screen.
7. Select OK once more to close Internet Options and you are done.
Now users will no longer be able to see what Web sites you visit from the cookies and Temporary Internet Files that are stored on your computer. Additionally, you will have freed up some disk space by deleting these files.
Tags : Clearing temporary Internet files and cookies, Internet
Read More >>
Posted by chanchandrue at 11:57 PM 0 comments
Clearing visited Web sites history

Clearing visited Web sites history
Internet Explorer, by default, is configured to record all of the Web sites that you visit for a 30-day period. If you are concerned about your privacy, your browsing history should be cleaned frequently and history settings configured best for privacy. Doing so will ensure that any user of your computer will not be able to easily see what you have been doing. Keep in mind, however, that if you get rid of the browser history, you will eliminate the ability to use the history to go back to Web sites for which you might have forgotten the URL.
That use is really the only reason I can think of that makes the browser history useful. If you can live without that convenience, then follow these steps to clear your history from your PC:
1. Open up a copy of Internet Explorer by using either the icon on the desktop or on the Start panel.
2. Once Internet Explorer is open, click the Tools menu bar item and select Internet Options.
3. Then, just click the Clear History button.
4. Your history will now be cleared. Because you still have Internet Options open on your screen, adjust the amount of days that your browsing history is stored.
5. As mentioned earlier, the default setting for this value is normally 30 days. Highlight the number in the days to keep pages in history box and type in 0 to maximize your privacy.
6. Then, click OK to save your changes and exit the Internet Options screen.
After you have cleared your browser history and modified the history setting, your privacy will be much easier to protect.
Tags : Clearing visited Web sites history, Web Sites
Posted by chanchandrue at 11:52 PM 0 comments
Locking down Internet Explorer
Now that you have removed all of the spyware and adware on your computer, let's turn off certain features of Internet Explorer so that you will be less likely to accidentally install more spyware. To get started, change the ActiveX install settings to prevent any new ActiveX apps to be installed. Follow these steps to change this setting:
1.Open Internet Explorer.
2.Click the Tools menu bar item and select Internet Options.
3.Click the Custom Level button on the Security tab.
4.Locate Download Signed ActiveX Control at the top of the list and select Disable.
5.Click OK and click Yes on the confirmation screen.
6.Select OK once more to close Internet Options.
A change in this setting can prevent you from installing new ActiveX controls from all Web sites, good and bad. If you ever run into some problem with a Web site not loading correctly, just re-enable this setting and try the site again.
Tags : Locking down Internet Explorer, Internet Explorer
Read More >>
Posted by chanchandrue at 11:48 PM 0 comments
Using WPA for a more secure wireless connection

Using WPA for a more secure wireless connection
Wi-Fi Protected Access, or WPA, is a new, improved security standard for wireless connections. WPA has addressed the weaknesses of WEP; it was developed to create a viable alternative to WEP that is more secure than that standard. The fundamentals are the same between the standards, but WPA has improved some of the various mechanisms that plagued WEP. For example, encryption keys are now dynamic and change often automatically. Additionally, the complexity of the encryption key has also been increased to help fight off users who try to derive a key from data that they capture. One of the largest improvements in WPA is the addition of authentication to the wireless connection. Now, users have to have the right encryption settings, as well as a valid username and password, to gain access to the network.
This new standard is just starting to gain momentum. Microsoft has released a special patch for Windows XP that adds this new standard to Windows. However, installing the patch will not allow you to use this new standard. Just as with WEP, WPA is programmed into the firmware of the hardware components. In order to use WPA, you must have hardware that specifically supports it. Currently, only a few companies offer base stations and wireless adapters that support this new method of security. However, that will change in time.
The next time you are considering purchasing a wireless base station and adapter, do some research and pick one that supports WPA to ensure that your wireless communications will not be decrypted and your privacy is secure.
Tags : Using WPA for a more secure wireless connection, Network Security, Wireless Connection
Read More >>
Posted by chanchandrue at 11:43 PM 0 comments
Using WEP for secure communication
Wired Equivalent Privacy, or WEP, is the first security standard for wireless networks. The basic concept for WEP security is to encrypt the data that is sent back and forth between the access point and the client adapter. This is done using various degrees of encryption strength. A special key, known as the encryption key, is used by computers to connect to a WEP-protected wireless network. This allows the client computer's adapter to be able to decrypt and also send
encrypted messages in the same language as the base station.
This standard sounds like a great way to secure a wireless network. However, it presents some flaws. The largest one is that the whole system relies on just one key. If someone's laptop is stolen that is part of a corporate network, the encryption key must be changed for the base station and for all of the other computers using the wireless connection. This change is necessary because the current encryption key could be easily extracted from the system settings.
Additionally, someone can potentially derive the encryption key by carefully analyzing the data they intercepted.
If you have a wireless base station, I highly recommend that you enable WEP to protect your home. Setting up WEP is different on every set of hardware, but the following are the basics:
1. Connect to your base station setting remotely using your Web browser. This address and port number varies, but usually is http://192.168.1.1 or http://192.168.2.1. Often, the port number is changed to 8080 so people donÕt think you have a Web server running. In that case, try http://192.168.1.1:8080 or http://192.168.2.1:8080.
2. Once you connect, you usually are asked for a password. For all Linksys hardware, the Username field is left blank and the password is admin. Other hardware manufacturers use some sort of a variation of the above. It also would be a good idea to change the password to something other than admin when you are working in the administration settings.
3. Locate the WEP settings and specify the encryption strength in bits. Then, come up with an encryption key and type that in. Write down your encryption key and strength for use in step 5.
4. Save your changes. You can now close the Web administration site.
5. The last part of setting up WEP is configuring the client computers that will connect to the base station. Once again, this information varies, depending on your wireless card. Consult the manual for your card to find out how to set up your card to use WEP.
Setting up WEP will greatly increase the security of your wireless network. Even though there are some flaws, it is much better than using no protection at all. It has the same effect as a car alarm. If a burglar has to choose between a car that clearly has an alarm or one that doesn't, which one will they choose to break into?
Tags : Using WEP for secure communication, Network Security
Read More >>
Posted by chanchandrue at 11:38 PM 0 comments
Disabling Messenger Service
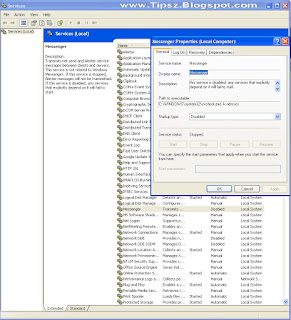
Disabling Messenger Service
Microsoft has included a service in the last few versions of Windows that allows system administrators to send pop-up messages to all computers on a local network. This service can be an invaluable resource for administrators who want to get the word out about some upcoming server maintenance. For example, end users would see a message pop up on their screens that notifies them that the work group file server will be inaccessible for the next hour while routine maintenance is performed.
This is a great service n when it is used correctly. Unfortunately, the Messenger Service has been abused. Just because any user can send messages to the entire work group doesn't mean that she or he should. This capability is sometimes not a good thing. Users that are part of large local area network, such as just about every Internet user, can send out a mass message to all users in the same subnet. As you can imagine, some users that know how to use the service have started to
abuse it by sending spam to all the users in their same subnet. Nowadays, you may get spam not only in your inbox but also in a pop-up window that could appear at any time.
The Messenger Service, just like any other service or program that is accessible to the outside world, increases your security risk. Although there is currently not an exploit for the Messenger Service that allows remote users to execute commands on your computer, who knows what the future will hold? To be safe, it is best to just disable this service. You will also be cutting down on a new type of spam.
Disabling the Messenger Service can be done by using the Service Manager. Follow these steps to get started:
1. Click the Start button and select Run.
2. Key in services.msc in the box and click OK.
3. The Services Manager will load. Scroll though the list and right-click Messenger and select Properties.
4. Change the Startup Type to Disabled.
5. Click the Stop button and then click OK to save your changes.
Now the Messenger Service is one less thing to worry about. You can kiss the annoying pop-up text ads goodbye and also reduce your risk for an attack in the future.
Tags : Disabling Messenger Service, Messenger
Read More >>
Posted by chanchandrue at 11:30 PM 0 comments
Disabling Remote Desktop connection
The Remote Desktop feature of Windows XP is a great way to be able to access your
computer when you are away from the office or home. However, if you have poor computer security, the Remote Desktop also is a great way for anyone to be able to access and control your whole computer. Remote Desktop is a very risky application to leave exposed to the world. Its security relies solely on your account password, which for most users is easy to guess.
If you do not use Remote Desktop, then it would be a good idea to disable the feature. Doing so is a snap. Just follow these steps to turn it off:
1. Right-click the My Computer icon on the desktop or in the Start Menu and select
Properties.
2. Click the Remote tab to expose the remote access settings.
3. Next, uncheck the box under Remote Assistance.
4. Uncheck the box under Remote Desktop as well.
5. Click OK to save your changes.
When Remote Desktop connections are disabled, you have one less thing to worry about namely, someone having the ability to break into your computer.
Tags : Disabling Remote Desktop connection, Remote Desktop
Read More >>
Posted by chanchandrue at 11:25 PM 0 comments
Configuring Windows firewall
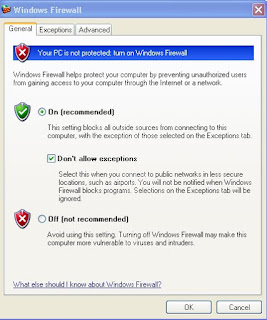
Configuring Windows firewall
Configuring the firewall to allow certain programs to work through it is not always the best thing to do, because it will expose your computer more to the outside world and increase your risk of getting infected with something. However, in the short term or for an application that you must use, you can make it work through the firewall. In the original version of the firewall, the only possibility was to specify a port number to open. Now, it is much easier to make an application work though the firewall. Instead of typing in a port number, users can just select the program on their computer that they want to have accessed through the firewall.
This capability makes the firewall configuration much more user-friendly. Additionally, in Service Pack 2, Microsoft left in the old way to open up the firewall manually by entering in a port number, so that users still have total control if they really want it. The end result of these two methods is the same; the only difference is the ease of use for less experienced Windows XP users.
Using the new feature to open up holes in the firewall is pretty cool. Follow these steps to open up the firewall for a specific application:
1. Open up Network Connections again by clicking the Start Menu and selecting Run. Then, type firewall.cpl in the box and click OK.
2. When the Windows Firewall settings window loads, click the Exceptions tab.
3. You will see a list of all of the different exceptions that are currently enabled, as signified by the check in the box. By default, a few applications will be enabled. I recommend that you uncheck all of the entries unless you use them. If not, then you are just taking an unnecessary risk by leaving those doors open.
4. If you want to add an application to the exception list so that it will be able to accept connections and data from the outside world, such as an Instant Message program that wants to receive files from other users, just click the Add Program button.
5. Select the name of the program from the list or click the Browse button on the Add a Program window to select the executable of the application that you want to open to the world.
6. When you are finished selecting the program that you want to be able to access through the firewall, click OK and it will appear on the list.
7. Now that the program is on the list, just check the box next to the name to open up the firewall for the application.
8. Click OK to activate your new firewall settings.
Windows Firewall also includes settings on how you want your computer to respond when several different standard Internet messages are sent to it. For example, one setting you can specify is the ping command, which is a network command used to estimate turnaround time between sending data to a computer and receiving a response. All of these settings are found on the Advanced tab by clicking the Settings button under the ICMP section. The screen is pretty straightforward. If you want your computer to have a stealth presence on the Web, as I mentioned earlier, you should uncheck all of the entries listed on the ICMP tab.
Tags : Configuring Windows firewall, Windows Read More >>
Posted by chanchandrue at 11:21 PM 0 comments
Disabling Unneeded Protocols
With every computer comes programs installed that you do not need. As with extra programs taking up space, extra protocols are just wasting your network connection and can actually slow it down. How is this possible? By default, a few different protocols are installed on your computer to allow for maximum compatibility with other computers on a network; these protocols each require bandwidth to operate. Most users will not use too many protocols, and their computers will use up a portion of their connection as they respond and transmit information for these protocols.
Additionally, with extra protocols installed on your network adapter connected to the Internet, you increase your risk of security-related problems. One of the most common risks for broadband users is that they have the Client for Microsoft Networks networking protocol enabled on their connection. This protocol allows everyone in their neighborhood to connect to the users computers and view any files that they may be sharing. This fact alone should be a good enough reason for you to turn off the extra protocols. But with them disabled, you will also save a little bandwidth as well.
Viewing protocols on your network adapters
Viewing the protocols installed and active on your various network adapters is easy. Just follow these quick steps and you will be viewing them in no time:
1. Right-click the My Network Places icon on the desktop or in the Start Menu and select Properties. If the My Network Places icon is not in either of those locations, then go to the Control Panel and click the Network Connections icon that is shown under the Classic view.
2. Next, right-click the network adapter with which you want to view the network protocols and select Properties.
3. This will bring up a list of the protocols installed as well as active on your adapter, as Figure 11-11 shows. The protocols that are installed but not active are indicated by the absence of a check in the checkbox.
Disabling a specific protocol
Now that you have the list of installed and active protocols on your screen, you are ready to disable a protocol. To do so, just click the check box to remove the check. Then click the OK button and the protocol is no longer active on the network adapter. I highly recommend that you disable all protocols except for the TCP/IP protocol (also referred to as the Internet Protocol). Doing so will optimize your adapter for speed and security.
Be aware that if you remove the Client for Microsoft Networks protocol and the file-sharing protocol, you will no longer be able to share your files. Additionally, you will no longer be able to connect to remote computers to view their shared files.
Also keep in mind that if you have multiple adapters in your machines, such as a wireless adapter, a wired network adapter, and a dialup modem, you will have to repeat the preceding instructions for each adapter.
Tags : Disabling Unneeded Protocols, Protocols
Read More >>
Posted by chanchandrue at 11:15 PM 0 comments
Assigning Alternative IP Addresses
One of the most common network-related delays occurs in the last moments of the system startup. The majority of computer users use dynamic network card configuration. There is nothing wrong with this feature, but under certain configurations, the user can experience delays when getting an IP address.
Every time you turn on your computer, it has to set up the IP configuration. Often, this setup can result in your computer pausing for moments during the loading process. The delay is a result of your PC waiting for the DHCP server (a DHCP server dynamically assigns addresse to computers connected to a network), which is the provider of the network information, to respond. In other situations, a user can experience a delay when a DHCP server is not present on the network.
If you use a dialup connection to the Internet, your computer will rely on getting a dynamic IP address from your service provider when you connect. When you first turn on your computer, it will search for a DHCP server to get an address for the local networking components of the operating system. This is occurring when your computer is still in the early boot stages and is not connected to your dialup ISP (Internet Service Provider). Because you are not connected to a network that has a DHCP server, such as when you are dialed up to your Internet provider, your computer may experience a delay, as the computer is searching for a DHCP server when there really is none available.
This hack will only work for users that have network cards and modems installed. It does not apply to users that just have modem connections to the Internet.
One easy solution to this problem is to assign alternative information to your network card. This task is actually pretty easy, as it does not require any major tampering. Follow these steps to specify an alternative IP configuration for your computer:
1. First, get into Network Properties. This can be accomplished by going to the Control Panel through the Start Menu.
2. Once you are in the Control Panel, make sure that you are in the Classic View,
and open Network Connections. If you are not in Classic View, just click the button on the left that states Switch to Classic View.
3. Now that you are in the Network Connections window, you will see a list of network adapters on your computer. Right-click the icon to which your network connection is hooked up and select Properties.
4. Doing so will launch a new window that lists the different protocols installed on the network card. Click the Internet Protocol (TCP/IP) to select it. Then click the Properties button.
5. Once the Internet Protocol (TCP/IP) Properties window is displayed, click the
Alternative Configuration tab. This is where you will have to enter in your data.
6. First, you will have to click the User Configured radio button to allow the text boxes to be edited.
7. Next, type in an IP address for your computer that will be used for the sake of speed in the event that your computer cannot get a DHCP address because you are using a dialup Internet connection. I recommend you use 192.168.1.X. Replace X with any unique number for each computer between 2 and 254. The exact IP address numbers that you choose do not matter. You just want to have a valid IP address filled in so that your
computer does not waste too much time looking for a DHCP address when there is no DHCP server giving out the address on your network.
8. Then, type in 255.255.255.0 as your Subnet Mask.
9. Your Default Gateway should be set to 192.168.1.1 because that is a valid gateway address. As I mentioned earlier, the exact numbers do not matter. We just want to have the computer assign some value instead of spending time searching when it will not find a DHCP server.
10. Then, enter in what your DNS servers should be. You can ask your ISP what they should be. But this information really isn't essential, as this configuration will almost never be used to connect to the Internet. It is just a default fallback in the rare case that you are having networking trouble. Feel free to leave these fields blank, as well as the WINS fields.
11. Click the OK button and then click the OK button for the network properties screen.
That's it; you are now finished.
Tags : Assigning Alternative IP Addresses, IP Address
Read More >>
Posted by chanchandrue at 11:09 PM 0 comments
short names long meaning
short names long meaning
A ---ADSL - Asymmetric Digital Subscriber Line
AGP - Accelerated Graphics Port
ALI - Acer Labs, Incorporated
ALU - Arithmetic Logic Unit
AMD - Advanced Micro Devices
APC - American Power Conversion
ASCII - American Standard Code for Information Interchange
ASIC - Application Specific Integrated Circuit
ASPI - Advanced SCSI Programming Interface
AT - Advanced Technology
ATI - ATI Technologies Inc.
ATX - Advanced Technology Extended
B ---
BFG - BFG Technologies
BIOS - Basic Input Output System
BNC - Barrel Nut Connector
C ---
CAS - Column Address Signal
CD - Compact Disk
CDR - Compact Disk Recorder
CDRW - Compact Disk Re-Writer
CD-ROM - Compact Disk - Read Only Memory
CFM - Cubic Feet per Minute (ft�/min)
CMOS - Complementary Metal Oxide Semiconductor
CPU - Central Processing Unit
CTX - CTX Technology Corporation (Commited to Excellence)
D ---
DDR - Double Data Rate
DDR-SDRAM - Double Data Rate - Synchronous Dynamic Random Access Memory
DFI - DFI Inc. (Design for Innovation)
DIMM - Dual Inline Memory Module
DRAM - Dynamic Random Access Memory
DPI - Dots Per Inch
DSL - See ASDL
DVD - Digital Versatile Disc
DVD-RAM - Digital Versatile Disk - Random Access Memory
E ---
ECC - Error Correction Code
ECS - Elitegroup Computer Systems
EDO - Extended Data Out
EEPROM - Electrically Erasable Programmable Read-Only Memory
EPROM - Erasable Programmable Read-Only Memory
EVGA - EVGA Corporation
F ---
FC-PGA - Flip Chip Pin Grid Array
FDC - Floppy Disk Controller
FDD - Floppy Disk Drive
FPS - Frame Per Second
FPU - Floating Point Unit
FSAA - Full Screen Anti-Aliasing
FS - For Sale
FSB - Front Side Bus
G ---
GB - Gigabytes
GBps - Gigabytes per second or Gigabits per second
GDI - Graphical Device Interface
GHz - GigaHertz
H ---
HDD - Hard Disk Drive
HIS - Hightech Information System Limited
HP - Hewlett-Packard Development Company
HSF - Heatsink-Fan
I ---
IBM - International Business Machines Corporation
IC - Integrated Circuit
IDE - Integrated Drive Electronics
IFS- Item for Sale
IRQ - Interrupt Request
ISA - Industry Standard Architecture
ISO - International Standards Organization
J ---
JBL - JBL (Jame B. Lansing) Speakers
JVC - JVC Company of America
K ---
Kbps - Kilobits Per Second
KBps - KiloBytes per second
L ---
LG - LG Electronics
LAN - Local Area Network
LCD - Liquid Crystal Display
LDT - Lightning Data Transport
LED - Light Emitting Diode
M ---
MAC - Media Access Control
MB � MotherBoard or Megabyte
MBps - Megabytes Per Second
Mbps - Megabits Per Second or Megabits Per Second
MHz - MegaHertz
MIPS - Million Instructions Per Second
MMX - Multi-Media Extensions
MSI - Micro Star International
N ---
NAS - Network Attached Storage
NAT - Network Address Translation
NEC - NEC Corporation
NIC - Network Interface Card
O ---
OC - Overclock (Over Clock)
OCZ - OCZ Technology
OEM - Original Equipment Manufacturer
P ---
PC - Personal Computer
PCB - Printed Circuit Board
PCI - Peripheral Component Interconnect
PDA - Personal Digital Assistant
PCMCIA - Peripheral Component Microchannel Interconnect Architecture
PGA - Professional Graphics Array
PLD - Programmable Logic Device
PM - Private Message / Private Messaging
PnP - Plug 'n Play
PNY - PNY Technology
POST - Power On Self Test
PPPoA - Point-to-Point Protocol over ATM
PPPoE - Point-to-Point Protocol over Ethernet
PQI - PQI Corporation
PSU - Power Supply Unit
R ---
RAID - Redundant Array of Inexpensive Disks
RAM - Random Access Memory
RAMDAC - Random Access Memory Digital Analog Convertor
RDRAM - Rambus Dynamic Random Access Memory
ROM - Read Only Memory
RPM - Revolutions Per Minute
S ---
SASID - Self-scanned Amorphous Silicon Integrated Display
SCA - SCSI Configured Automatically
SCSI - Small Computer System Interface
SDRAM - Synchronous Dynamic Random Access Memory
SECC - Single Edge Contact Connector
SODIMM - Small Outline Dual Inline Memory Module
SPARC - Scalable Processor ArChitecture
SOHO - Small Office Home Office
SRAM - Static Random Access Memory
SSE - Streaming SIMD Extensions
SVGA - Super Video Graphics Array
S/PDIF - Sony/Philips Digital Interface
T ---
TB - Terabytes
TBps - Terabytes per second
Tbps - Terabits per second
TDK - TDK Electronics
TEC - Thermoelectric Cooler
TPC - TipidPC
TWAIN - Technology Without An Important Name
U ---
UART - Universal Asynchronous Receiver/Transmitter
USB - Universal Serial Bus
UTP - Unshieled Twisted Pair
V ---
VCD - Video CD
VPN - Virtual Private Network
W ---
WAN - Wide Area Network
WTB - Want to Buy
WYSIWYG - What You See Is What You Get
X ---
XGA - Extended Graphics Array
XFX - XFX Graphics, a Division of Pine
XMS - Extended Memory Specification
XT - Extended Technology
Tags : short names long meaning, Short Names
Read More >>
Posted by chanchandrue at 11:01 PM 0 comments
Maximize Dial-up Modem Settings
Did you know that by changing a few settings you can make your dial-up modem run better? That's right you might have a fast modem and a good connection, but you are not getting the best performance. With a few adjustments, you can get faster connection speeds.
NOTE: Since every PC configuration is different, these adjustments might not work for everyone.
With Windows 95, 98 & ME you'll need to open your Control Panel ( Start / Control Panel ). Click "System" then choose "Device Manager". Open up "Ports", highlight your modem port (should be COM2), and choose "Properties" near the bottom. When you click "Port Settings", you will see the modem speed listed under "Bits per second".
With Win XP , just hold down the Alt key and double-click "My Computer" to bring up System Properties. Click the "Hardware" tab, then choose the "Device Manager" button. Scroll down to "Modems" and click the little (—) to show your modem, then double click it.
Selecting the "Modem" tab will allow you to adjust the port speed.
Usually, the Maximum Port Speed is on the highest setting (115,000 bps), but sometimes you will find it on a slower default of 9600 bps. If you have a 56k modem, you can crank it up to the maximum setting without any trouble (in most cases). If you live in a cave and have a 28k modem, then the fastest you can do is 57,600 bps.
Win 9x users should also adjust the "Flow Control" near the bottom. The default for this is usually Xon/Xoff which is the software control—change this to "Hardware" if you want to get the most from your modem. Next, click the "Advanced" button to adjust the Receiver Buffer to its highest setting (all the way to the right). If you run into any problems, just turn this one back to the 2/3 setting.
To check/adjust the Receive-Transmit buffers in XP, click the "Advanced" tab of your modem properties then choose the "Advanced Port Settings" button. Make sure that both are set to their highest settings.
There are many more tweaks that can be done in the registry, but the potential for disaster is too high for the average user. Some folks install dial-up accelerators, which basically tweak these registry settings for you and perform other routines to optimize performance.
Just by changing these few settings, though, you should see better performance.
Tags : Maximize Dial-up Modem Settings, Dial-Up
Read More >>
Posted by chanchandrue at 10:57 PM 0 comments
Advanced Google Search
Advanced Google Search
Google is clearly the best general-purpose search engine on the Web.But most people don’t use it to its best advantage or in an advanced way. Do you just plug in a keyword or two and hope for the best? That may be the quickest way to search, but with more than 3 billion pages in Google’s index, it’s still a struggle to pare results to a manageable number. There are some ways in which advanced Google search can be used to get the desired results.
But Google is an remarkably powerful tool that can ease and enhance your Internet exploration. Advanced Google search options go beyond simple keywords, the Web, and even its own programmers. Let’s look at some of the advanced Google search options.
Syntax Search Tricks
Using a special syntax is a way to tell Google that you want to restrict your searches to certain elements or characteristics of Web pages.Here are some advanced Google search operators that can help narrow down your search results.
1.Intitle: at the beginning of a query word or phrase restricts your search results to just the titles of Web pages.
2.Intext: does the opposite of intitle:, searching only the body text, ignoring titles, links, and so forth. Intext: is perfect when what you’re searching for might commonly appear in URLs. If you’re looking for the term HTML, for example, and you don’t want to get results such as
www.tipsz.blogspot.com/
you can enter intext:html
3.Link: lets you see which pages are linking to your Web page or to another page you’re interested in. For example, try typing in
link:http://www.tipsz.blogspot.com/
3.site: (which restricts results to top-level domains) with intitle: to find certain types of pages. For example, get scholarly pages about Mark Twain by searching for intitle:”Mark Twain”site:edu. Experiment with mixing various elements; you’ll develop several strategies for finding the stuff you want more effectively. The site: command is very helpful as an alternative to the mediocre search engines built into many sites.
Swiss Army Google
Google has a number of services that can help you accomplish tasks you may never have thought to use Google for. For example, the new calculator feature
(www.google.com/help/features.html#calculator) lets you do both math and a variety of conversions from the search box. For extra fun, try the query “Answer to life the universe and everything.”
Suppose you want to contact someone and don’t have his phone number handy. Google can help you with that, too. Just enter a name, city, and state. (The city is optional, but you must enter a state.) If a phone number matches the listing, you’ll see it at the top of the search results along with a map link to the address. If you’d rather restrict your results, use rphonebook: for residential listings or bphonebook: for business listings. If you’d rather use a search form for business phone listings, try Yellow Search
(www.buzztoolbox.com/google/yellowsearch.shtml).
Let Google help you figure out whether you’ve got the right spelling—and the right word—for your search. Enter a misspelled word or phrase into the query box (try “thre blund mise”) and Google may suggest a proper spelling. This doesn’t always succeed; it works best when the word you’re searching for can be found in a dictionary. Once you search for a properly spelled word, look at the results page, which repeats your query. (If you’re searching for “three blind mice,” underneath the search window will appear a statement such as Searched the web for “three blind mice.”) You’ll discover that you can click on each word in your search phrase and get a definition from a dictionary.
Extended Googling
Google offers several advanced services that give you a head start in focusing your search. Google Groups (http://groups.google.com/)
indexes literally millions of messages from decades of discussion on Usenet. Google even helps you with your shopping via two tools: FroogleCODE(http://froogle.google.com/),
which indexes products from online stores, and Google CatalogsCODE(http://catalogs.google.com/),
which features products from more 6,000 paper catalogs in a searchable index. And this only scratches the surface. You can get a complete list of Google’s tools and services at
www.google.com/options/index.html
You’re probably used to using Google in your browser. But have you ever thought of using Google outside your browser?
Google Alert
(http://www.googlealert.com/)
monitors your search terms and e-mails you information about new additions to Google’s Web index. (Google Alert is not affiliated with Google; it uses Google’s Web services API to perform its searches.) If you’re more interested in news stories than general Web content, check out the beta version of Google News Alerts
(www.google.com/newsalerts).
This advanced Google service (which is affiliated with Google) will monitor up to 50 news queries per e-mail address and send you information about news stories that match your query. (Hint: Use the intitle: and source: syntax elements with Google News to limit the number of alerts you get.)
Google on the telephone? Yup. This service is brought to you by the folks at Google Labs
(http://labs.google.com/),
a place for experimental Google ideas and features (which may come and go, so what’s there at this writing might not be there when you decide to check it out).
With Google Voice Search
(http://labs1.google.com/gvs.html),
you dial the Voice Search phone number, speak your keywords, and then click on the indicated link. Every time you say a new search term, the results page will refresh with your new query (you must have JavaScript enabled for this to work). Remember, this service is still in an experimental phase, so don’t expect 100 percent success.
In 2002, Google released the Google API (application programming interface), a way for programmers to access Google’s search engine results without violating the Google Terms of Service. A lot of people have created useful (and occasionally not-so-useful but interesting) applications not available from Google itself, such as Google Alert. For many applications, you’ll need an API key, which is available free fromCODE www.google.com/apis
Tags : Advanced Google Search, Google
Read More >>
Posted by chanchandrue at 10:47 PM 0 comments
Best 3 Ways online money
2) Adbrite is an advertising the site offers links and image like Google Adsense ads and you’ll be paid according to the price offered advertising in accordance with the contents of the site content and your payment will be calculated once for the site at Adbrite, and I do not really know how you will get a commission from the ad is clicked and to register on Adbrite more easily than register to Google Adsense.
3) BidVertiser is a site advertising a very high demand by middle-lower sites and ads that will appear in the form of a link BidVertiser and the results obtained large enough to register this BidVertiser you do not need to have a Good PageRank or Alexa Rank.
Tags : Best 3 Ways online money, Online Money, Google Adsense, Adbrite, BidVertiser
Read More >>
Posted by chanchandrue at 10:33 PM 0 comments
Removing Stored User Name and Password in Mozila Firefox
Removing Stored User Name and Password in Mozila Firefox

When you visit a Web site that requires authentication or attempt to connect to remote computers, you are given the option to save your password so that the next time you visit the page or attempt to access a remote resource, you do not have to reenter your password. This feature can be a huge convenience, especially if you access a particular Web site or resource frequently. The downside to this convenience is the potential for horrible security and privacy problems. Essentially, you are taking the password off all of the sites and resources for which you saved a password. Anyone who has physical access to your computer can get in using your username and password, even if they do not know your password.
1. Open Mozila Firefox.
2. Click on Tools -> options -> Security -> Seved Passwords -> Show Passwords -> Yes.
3. The Stored User Names and Passwords window will load, showing you a list of all of the accounts that are saved on your computer.
4. To remove a saved password, select the account on the list and click the Remove
button.
5. Repeat the previous steps for any other accounts that you want to remove.
6. When you are finished, just click Close.
You can also use the Stored User Names and Passwords window to add more user names and passwords to your computer.
Tags : Username and Pasword, Mozilla Firefox, Removing Stored User Name and Password in Mozila Firefox,
Read More >>
Posted by chanchandrue at 10:20 PM 0 comments
Auto Disconnect Internet Explorer

Auto Disconnect Internet Explorer
Use this edit to automatically disconnect from Internet Explorer after a specified length of time has elapsed. Use this trick on anyone whom you don?t like using your computer with net J
Go to Start -> Run -> and type run in Regedit.
Go to: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanmanServer\Parameters
Modify/Create DWORD Value of Data type REG_DWORD Named [Autodisconnect]
Value Data: [Enter a new disconnect time. Use Hexadecimal if you are unfamiliar with Binary]
Exit Registry / Reboot
Tags : Auto Disconnect Internet Explorer
Read More >>
Posted by chanchandrue at 1:43 AM 0 comments
Stop Windows Messenger Autostart
Stop Windows Messenger Autostart
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\MSMSGS
Tags : Stop Windows Messenger Autostart Read More >>
Posted by chanchandrue at 1:37 AM 0 comments
Speed Up Internet
Speed Up Internet
Your computer slow down when you browse your local area network and connect to other computers that are sharing data? One of the most common causes of this slowdown is a feature of Windows Explorer that looks for scheduled tasks on remote computers. This effort can take some time on some computers and can really slow down your browsing. The window with which you are browsing the network may appear to freeze momentarily, as the system is waiting for a response from the remote computer.
Windows XP: Speeding Disk Access
Although this problem is a complex one, the solution is very simple. Instead of having to wait for the remote scheduled tasks, which is useless information to anyone who is not a system administrator remotely configuring scheduled tasks, you can disable this feature.
In order to do this, you will have to change the System Registry and delete a reference to a key so that this feature will not be loaded. To do this, follow these steps:
1. Open up the Registry Editor by clicking the Start Menu and selecting Run. Then type regedit in the text box and click the OK button.
2. Once the Registry Editor has loaded, expand the HKEY_LOCAL_MACHINE key.
3. Next, expand Software and then Microsoft.
4. Locate Windows and expand that as well.
5. You will want to be editing the main system files, so expand CurrentVersion.
6. Because this feature is a feature of the Windows component known as Explorer, expand the Explorer key.
7. Next, you will want to modify the remote computer settings, so expand the RemoteComputer key and then expand the NameSpace key to show all of the features that are enabled when you browse to a remote computer.
8. In the NameSpace folder you will find two entries. One is "{2227A280-3AEA-1069-A2DE-08002B30309D}" which tells Explorer to show printers shared on the remote machine. The other, "{D6277990-4C6A-11CF-8D87-00AA0060F5BF}," tells Explorer to show remote scheduled tasks. This is the one that you should delete. This can be done by right-clicking the name of the key and selecting Delete.
Tip:
If you have no use for viewing remote shared printers and are really only interested in shared files, consider deleting the printers key, "{2227A280-3AEA-1069-A2DE-08002B30309D}", as well. This will also boost your browsing speed.
Once you have deleted the key, you just need to restart and the changes will be in effect. Now your network computer browsing will be without needless delays.
Tags : Speed Up Internet
Read More >>
Posted by chanchandrue at 1:31 AM 0 comments
Speed Up Internet
Windows XP
1. First, open the Windows Registry using Regedit, and navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\ServiceProvider
2. Note the following lines (all hex dwords):
Class = 008 ( biggrin.gif - indicates that TCP/IP is a name service provider, don't change
LocalPriority = 1f3 (499) - local names cache
HostsPriority = 1f4 (500) - the HOSTS file
DnsPriority = 7d0 (2000) - DNS
NetbtPriority = 7d1 (2001) - NetBT name-resolution, including WINS
3. What we're aiming to do is increase the priority of the last 4 settings, while keeping their order. The valid range is from -32768 to +32767 and lower numbers mean higher priority compared to other services. What we're aiming at is lower numbers without going to extremes, something like what's shown below should work well:
4. Change the "Priority" lines to:
LocalPriority = 005 (5) - local names cache
HostsPriority = 006 (6) - the HOSTS file
DnsPriority = 007 (7) - DNS
NetbtPriority = 008 ( biggrin.gif - NetBT name-resolution, including WINS
5. Reboot for changes to take effect
2. Windows 9x/ME
1. The tweak is essentialy the same as in Windows 2000/XP, just the location in the Registry is slightly different. For a more detailed description see the Windows 2000/XP section above
2. Open the Windows Registry using Regedit, and (after backing up) navigate to:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\VxD\MSTCP\ServiceProvider
3. You should see the following settings:
Class=hex:08,00,00,00
LocalPriority=hex:f3,01,00,00
HostsPriority=hex:f4,01,00,00
DnsPriority=hex:d0,07,00,00
NetbtPriority=hex:d1,07,00,00
4. The "priority" lines should be changed to:
LocalPriority=hex:05,00,00,00
HostsPriority=hex:06,00,00,00
DnsPriority=hex:07,00,00,00
NetbtPriority=hex:08,00,00,00
5. Reboot for changes to take effect
3. System.ini IRQ Tweak - Windows 9x/ME ONLY
1. Find your Network Card's IRQ
1. In order to add the entry to your System.ini file, you'd first have to find your NIC's IRQ
2. Right-click on My Computer icon on your Desktop, then left-click on Properties (a shortcut for that would be to press the 'Windows' + 'Pause' keys). Navigate to Device Manager and double-click on Computer. Under "View Resources" you will find a list of IRQs, each with description of the device that's using it. Note the IRQ number used by your Network Adapter
2. Adding the entry to System.ini
1. Once you've found the IRQ of your Network Card, you need to reserve some RAM for its use, by adding an entry to the System.ini file. You can edit the file in any text editor, however the easiest way is to use Windows' built in "System Configuration Editor"
2. Navigate to Start > Run and type sysedit . Find the [386enh] Section in the System.ini file and add Irq[n]=4096 under it, where [n] is the IRQ number of your NIC and 4096 is the amount of RAM you want to reserve in Kbytes. We recommend using 4096, however you can experiment with different values if you want. Save changes in the file, exit and reboot for changes to take effect.
Note: If you choose to try different values, keep in mind that reserving too much RAM for your NIC will decrease the amount of RAM available for applications, while reserving too little might not give the desired effect
3. Additional Thoughts
1. The only negative effect of the System.ini IRQ tweak is that it will reduce the amount of RAM available for running applications a bit, by reserving some specifically for your Network Card's use. The gain in performance usually outweighs the negative effect by far, considering any Computer with 32Mb of RAM or more
2. This tweak may or may not work for you. It is not a documented tweak by Windows.
3. Keep in mind that if you add hardware to your system the IRQ of the Network Adapter might change, in which case you will need to modify the setting in System.ini
4. In systems with multiple NICs, you might want to add the setting for both IRQs. Also, you could reserve RAM for other IRQs if you wish, just use common sense and don't forget it reduces the amount of RAM available for running applications.
5. If you are using an USB device, it does not have a specific IRQ, however you can try adding the entry using the IRQ of the USB Controller.
6. For internal Cable Modems, you'd have to add the entry using the IRQ of your modem, rather than the IRQ of a Network Card
Tags : Speed Up Internet
Read More >>
Posted by chanchandrue at 1:21 AM 0 comments
Adjusting your cookie security policy
Adjusting your cookie security policy
If you do not want your computer to accept third-party cookies so that marketing companies cannot identify what ads they have shown you, or if you just want to adjust your cookie acceptance settings, then follow these steps:
1. Open Internet Explorer.
2. Click the Tools menu bar item and select Internet Options.
3. Click on Privacy tab.
4. You will see the up and down slider that allows you to select different levels of cookie security. I recommend that you bypass this and just click the Advanced button instead.
5. Once you click the Advanced button and see the Advanced Privacy Settings window, check the box that says Override Automatic Cookie Handling.
6. Your settings for first- and third-party cookies will now be available for adjustment. I recommend that you always accept first-party cookies. You can decide if you want to block or select the prompt to accept third-party cookies. Prompt will pop up a dialog box notifying you that a cookies request has been received.
7. Once you are finished with your settings, click the OK button to save your changes and return to Internet Options.
8. Click OK once more to close Internet Options.
Now that you have set the cookie privacy setting manually. you can eliminate cookies from being stored on your hard drive in the first place. Doing so will allow you to protect your privacy and still be able to use Web sites that need cookies.
Tags : Adjusting your cookie security policy, Security Policy
Read More >>
Posted by chanchandrue at 1:16 AM 0 comments
Update My Computer
What are updates?
Microsoft offers important updates, which include security and other critical updates, to help protect your computer against new viruses and other security threats that can spread over the Internet or a network. Other updates contain enhancements, such as upgrades and tools that can help your computer run more smoothly.
Update your Computer Follow This Steps:
1. Click Start, and then click Control Panel.
2. Depending on which Control Panel view you use, Classic or Category, do one of the following:
Click System, and then click the Automatic Updates tab.
Click Automatic (recommended) Option and select the day and time you want Windows to install updates. (Your Select Time Every Day 3:00 AM. Your Computer Update Every Day 3:00 AM)
Click Apply -> OK.
Tags : Update My Computer
Read More >>
Posted by chanchandrue at 1:12 AM 0 comments
Improving Web Site Security
Even the best firewalls, Secure Sockets Layer (SSL) and other protective measures will not enough to guard Web applications against every attack. It is infinitely more difficult for security professionals to figure out what new and innovative trick will be used to bypass security than it is for the hackers to find that trick
It can seem as if there is no solution to this problem. What is needed is a program that can check Web applications and further improve the security. That program is Acunetix WVS. It deals specifically with SQL Injection and other vulnerabilities like XSS. It helps to secure Web sites from harsh attacks, checks for scripting in cross-sites, and strengthens the authentication pages and passwords. It also audits shopping carts in an effort to prevent attacks. With the security audit reports peace of mind can finally be gained.
CRLF injection, directory traversal, code execution and file inclusion attacks are other ways to cripple a Web site's security. Authentication as well as input validation attacks are also likely.
The Google Hacking Database (GHDB) can identify important data like the logon pages, network information and so on and so forth that might be vulnerable, making it an important tool to improving Web site security. With the Acunetix, the queries wedged in the Google Hacking Database will be launched long before something goes wrong.
Acunetix gives suggestions on how to correct any problems through its report generator that will create quick reports and data to zero in any vulnerabilities that might exist.
It is necessary to reconstruct HTTPs and analyze them for cross-site scripting and SQL injection to ensure better security. Also important is HTTP fuzzer to validate the input and test the overall performance of the Web site.
It’s vital that passwords be configured and protected. Input configuration should utilize HTML form fillers as a matter of course. This allows testing how certain occasions and different inputs influence how the site behaves.
Important things to consider:
1. Is the Web site ready and prepared for a dictionary attack?
2. Support from other technologies such as PHP, CGI and ASP.
3. Search directories for weak permissions
4. Detect errors in pages as early as possible
5. Re-auditing all changes in the Web site to check for new vulnerabilities
dotDefender 2.1 is one of the programs that can protect and secure. It takes care of spammer bots, attacks, probes, SQL injections, hijackings, pronounced tampering and even proxy takeovers.
It can be a daunting task to improving Web site security, but is absolutely critical to do so. By following a few simple steps and using programs tailored to assist in the task everything will work efficiently and effectively.
Tags : Improving Web Site Security, Security Web, Hacking
Read More >>
Posted by chanchandrue at 1:07 AM 0 comments
Promote Your Site For Free
Web Directory Submission
Submitting your site in free directories is one of the easiest way to get traffic. Free directory submission may not get you a lot of traffic but it will certainly increase your rank in search engines. For free directories search "directory" in google.com. Here are the some free submission directories that I found for you. One thing you have to keep in mind is, when you submitting your site, make sure to choose the category that suits best to your site. Just submitting to any category does not send you targeted visitors.
Search Engine Submission
There are many websites offers free web submission. However, I prefer submitting my site manually. You can do this free at yahoo, google, jayde, and alexa. If you want to use web submission services then I strongly recommend WEB CEO. Web CEO comes free and provides great functionalities such as URL submission to more than 200 search engines, link exchange, keyword analyses and many more.
Link Exchange
Link exchange is another way to get free traffic to your website. However, you need to be selective, when it comes to choose the sites for link exchange. If you exchange links with similar sites to yours, that would help your page ranking. Also try to put your links in high ranking websites as it also helps your search engine ranking. Just be nice to the webmaster and ask for link exchange. In most cases they will say no but don't give up. (If you be nice I can exchange link with you as well).
Emails ( NOT SPAM )
One of the best ways to get free traffic is emails. Just let your friends know about your website. Use your website URL as your signature in all your mails. Also you can ask your friends to do the same for you. Every ones a while send newsletters to your friends about your website and ask them to forward this to their contacts. You will be surprised how much traffic you will get from this. Also I have to mention this DO NOT SPAM.
Forums and Groups
There are lots of discussion forums and groups available that discuss about various topics. You can become members to these forums. Post regular comments to these forum by using your URL as your signature. Just don't send your URL as it will look really unprofessional and you will end up excluded. Talk about whatever the group or forum is about. BECOME A REGULAR.
Blogs
Create blogs that links to your website. You can easily set up a blog for free. Google, yahoo, msn are provides free blog hosting services.
Tags : Promote Your Site For Free, blog, Forums and Groups, Emails ( NOT SPAM ), Link Exchange, Search Engine Submission, Web Directory Submited
Read More >>
Posted by chanchandrue at 12:59 AM 0 comments
How to Secure Facebook Account
How to Secure Facebook Account
How to Secure Your facebook Account?
Facebook users do not read the Facebook official blog might have missed the important updates on privacy and security enhancements. Facebook latest features are added as opt-in features, which probably means that majority of Facebook members might have not turned on or enabled them yet on their accounts.
Here are the important changes and short guides to improve and fully protect the login, password, and security of your Facebook profile.
Protect and Secure Facebook Account
Some of the latest features are about Facebook login safety. That includes a very strong account password. A strong password means you have to combine letters, special characters, and numbers. Make your password at least 10 characters long. But, for safety, it is recommended to make it 15 or more characters.
Add Your Mobile Numbers
Following This steps:
Image 1

Image 2

Image 3

1. Log in to Facebook.
2. On the top right of your screen, click on Account.
3. Select Account Settings.
4. Look your Left side Mobile Tab. Click on Mobile Tab.
5. Click on +Add a Phone Tab. ( View Image 1)
6. Open New Windows Automatic. Click on Add your phone number here ( View Image 2)
7. Open New Windows Automatic. and Type your Mobile Number in the Phone Number field. ( View Image 3)
8. Click on the Confirm button. and open New Windows.
9. Your Mobile inbox in Sent Confirm Code.
10. Type your Code in the Code field.
11. Click on the Confirm button.
How to Change Facebook password?
If you want to edit your password and make it a strong one, follow these steps:

1. Log in to Facebook.
2. On the top right of your screen, click on Account.
3. Select Account Settings.
4. Look for Password.
5. Click on Edit Password.
6. In the Current Password field, type your current password.
7. Type your New strong password in the New Password field.
8. Re-type your new strong password in the Confirm Password field.
9. Click on the Save Changes button.
Benefits of Secure Browsing
When you turn this feature on, your activities on Facebook becomes encrypted, this means it will be harder for anyone else to access your Facebook account without your knowledge and permission. This feature is not currently available for Facebook mobile browsing.
Login Notifications
Login Notifications feature alerts you by sending an email each time your Facebook account is accessed from a new computer or mobile device.
Follow this steps:
1. Log in to Facebook.
2. On the top right of your screen, click on Account.
3. Select Account Settings.
4. Look your Left side Security Tab. Click on Security Tab.
5. Click On Login Notifications Tab.
6. Check the box under Email and Text message.
7. Click on the Save Changes button.
Login Approvals
Login Approvals is a security feature similar to Login Notifications, but with an extra security step. With Login Approvals, each time you try to log in to your Facebook account from an unknown device such as any computer or mobile phone you haven't named and saved to your Facebook settings, you will first have to enter a security code that's been sent to your mobile phone.
To turn on your account's Secure Browsing (https), Login Notifications, and Login Approvals settings:
1. Log in to Facebook.
2. On the top right of your screen, click on Account.
3. Select Account Settings.
4. Look your Left side Security Tab. Click on Security Tab.
5. Check the box under Browse Facebook on a secure connection (https) when possible.
6. Click on the Save Changes button.
Let us know what you think about improving and upgrading your Facebook account protection by adding a comment below. submit your any problems in comment and i solve your problems.
Tags : How to Secure Facebook Account, Facebook
Read More >>
Posted by chanchandrue at 12:49 AM 0 comments














